Mina Security Design
Transaction Checks
Unsigned transactions checker
We check the pubkey bytes of the sender and all the accounts involved in the transaction to see if any of them are in the Mina Security Database. If any of these accounts are found in the Mina Security Database, we send the user a scam alert.
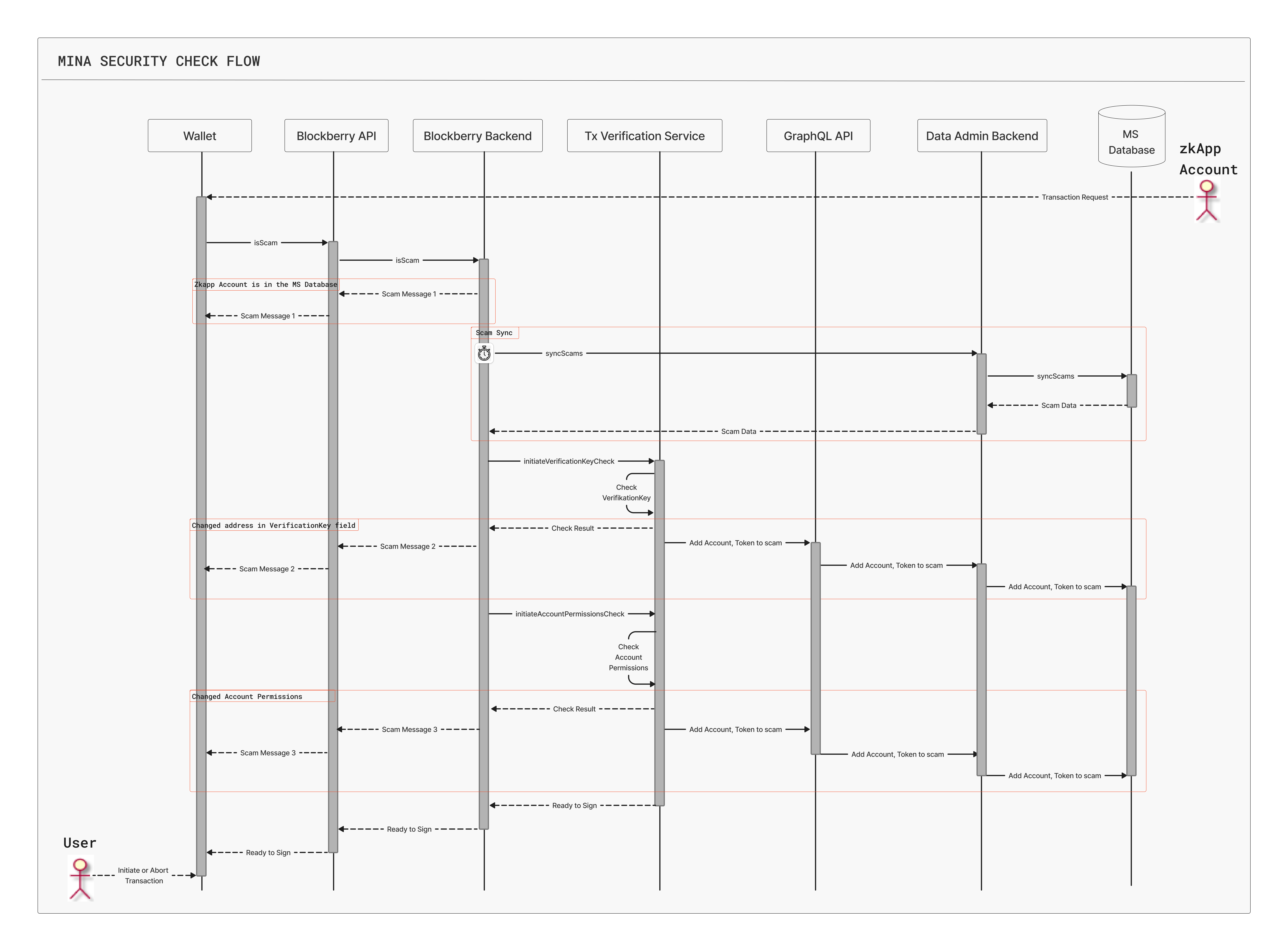
The check follows this flow:
- A sender initiates the transaction.
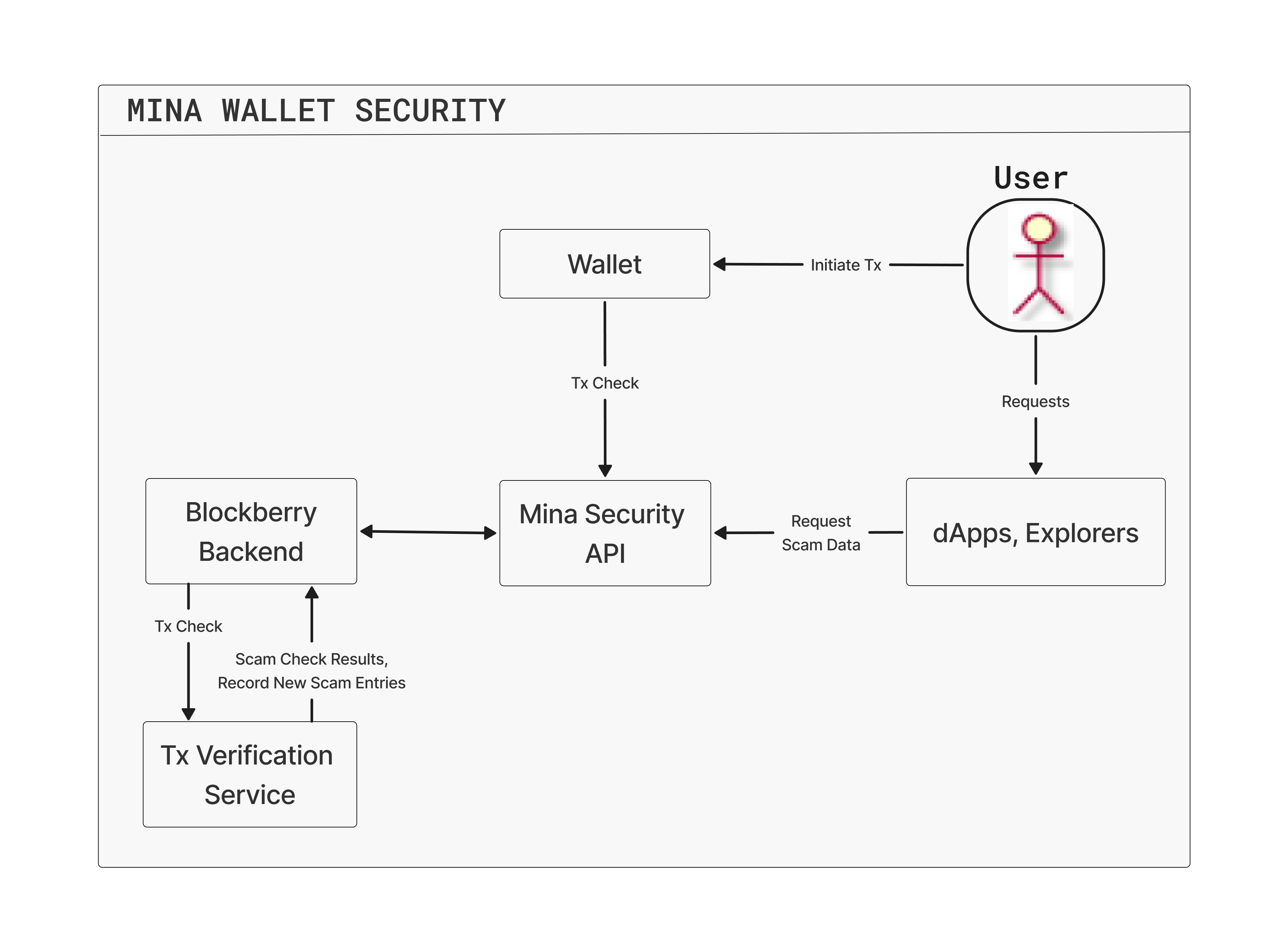
- The wallet or zkApp uses a Blockberry API endpoint to get the queried data.
- The Blockberry API queries the data through the Mina Security Backend.
- The Mina Security Backend requests the Transaction Verification Service to conduct the check.
- The Transaction Verification Service checks if any of the addresses of the accounts involved in the transaction are in the Mina Security Database.
- If so, we send the user a scam alert; otherwise, the transaction can proceed unalerted.
Receiving a scam alert doesn't mean that the transaction can't be run. It's up to a user whether to proceed the transaction upon receiving one. However, from now on, the user is solely responsible for any further action. We urge you to show extreme caution when receiving a scam alert!
Verification Key Change
Every zkApp account has a verification key stored on-chain. The verification key is used to verify off-chain proofs. A sign of a scam is when the verificationKey field in the Account Updates has the sender’s address in the public key. It means that a scam account enters its address hash in the verificationKey field and can potentially hijack the user's account to drain it using this flow:
- A zkApp account requests a user to sign a transaction containing the verificationKey field.
- The zkApp account enters its address hash in the public key.
- The user doesn’t see this in the wallet application and signs the transaction. The scam zkApp account takes over the user's account and drains it or changes the private key, resulting in the user losing control over their funds and account.
Therefore, we run a check to find if the verification key has been changed in the past and whether this was done multiple times. This check follows this flow:
- A sender initiates the transaction.
- The wallet or zkApp uses a Blockberry API endpoint to get the queried data.
- The Blockberry API queries the data through the Mina Security Backend.
- The Mina Security Backend requests the Transaction Verification Service to conduct the check.
- The Transaction Verification Service checks if the verificationKey field in the accountUpdates has been changed and whether it happened multiple times.
- If there have been multiple verification key changes, we send the user a scam alert; otherwise, the transaction can proceed unalerted.
Verification key change is not exactly a direct indication of a scam activity. In fact, it happens quite regularly. However, if the verification key was changed repeatedly and regularly, this can definitely pose a scam threat, of which we warn users.
The diagram below shows how the Mina Security Service runs transaction checks.